vCenter 7.0 U2: vSphere Native Key Provider! (integrated KMS)
Recently vCenter 7.0 Update 2 was released to the public, with new features and improvements. For me one highlight was the introduction of the "vSphere Native Key Provider" (NKP): a native KMS (Key Management Server), or now also called "Key Provider". This allows using features like VM-Encryption, vSAN Encryption or virtual TPMs without spinning up or buying an external KMS server from 3rd-party-vendor.
However as noted in the documentation regarding NKP this is not meant to replace existing key servers and does not have full functionality like other key provider-solutions. However it’s a great addition for HomeLabs, smaller organizations or as a temporary solution when migrating to an external one.
The configuration
Creating and configuring a Key provider is done real quick.
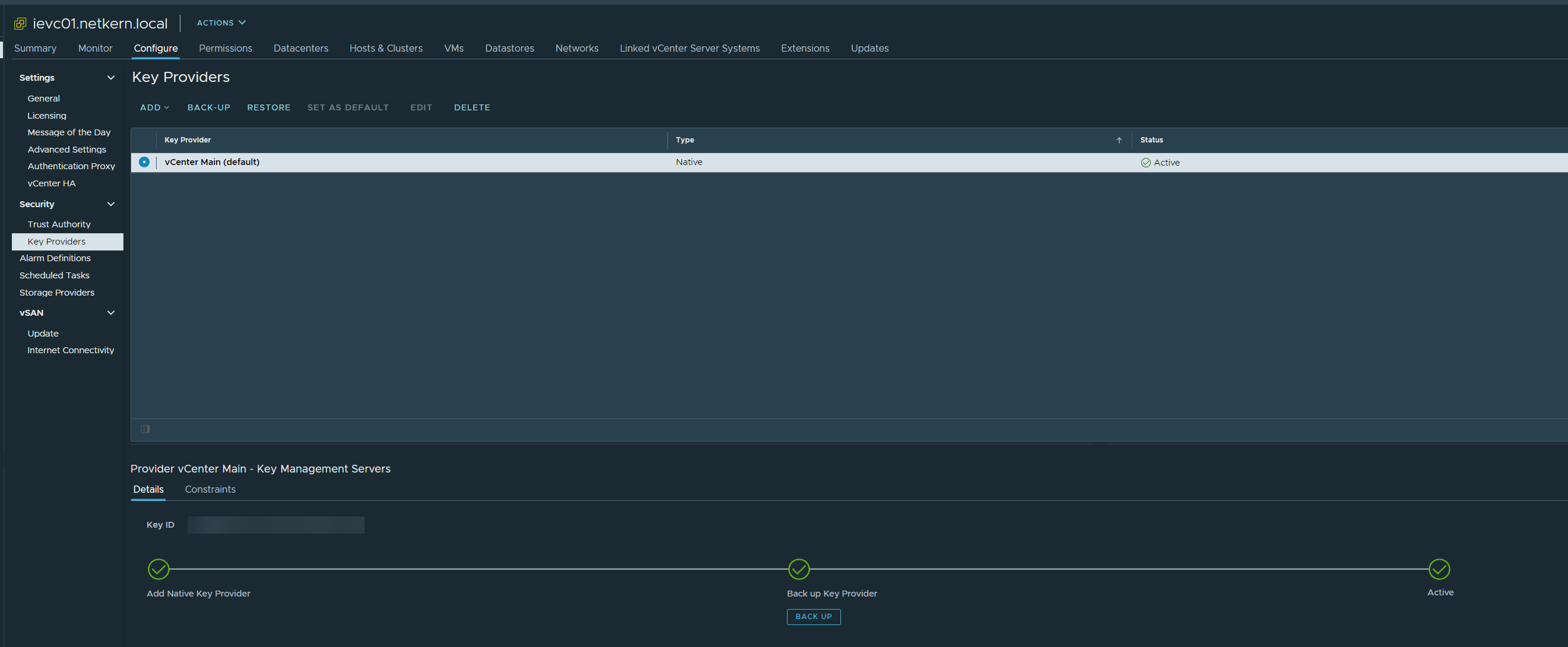
- Click on the vCenter in the inventory
- Go to Configure – Security – Key Providers
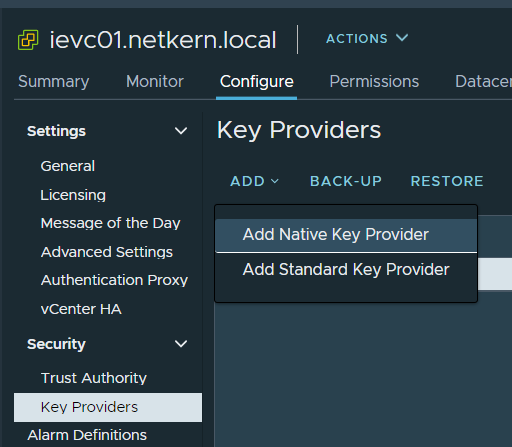
- Click on Add – Add Native Key Provider
- Give it a name, and decide if it should work only on hosts with a TPM.
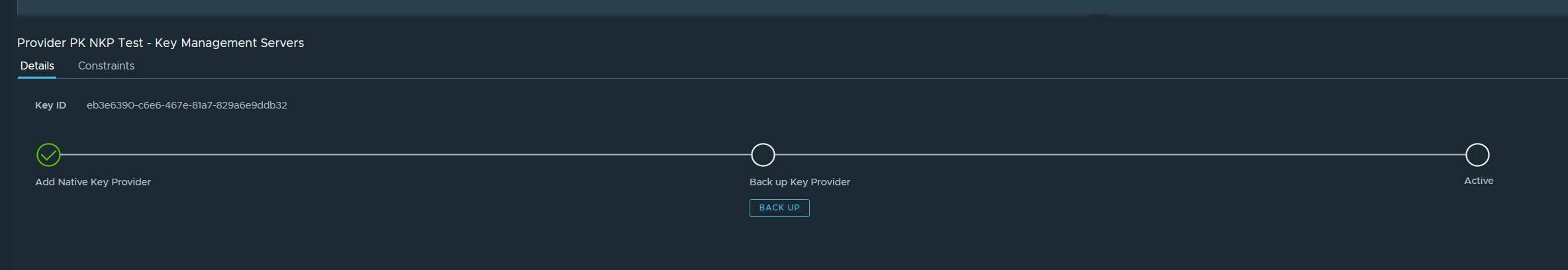
- As the last step you need to backup and download the key so that the Key Provider gets active and can be used.
Your Key Provider is now ready to be used in your environment.
After configuring vCenter Server pushes the primary key to all ESXi hosts which then generate data encryption keys, which can take a few minutes. Also when deleting or updating a NKP the change is pushed to the hosts.
Additional information
Q: Can I use the Native Key Provider on multiple vCenters? (including Enhanced-Link-Mode)
Yes. If, for whatever reasons, you want to use the same private key/NKP on multiple vCenter instances you can backup/export the current key and simply re-import it into the desired vCenter.
This can particular be useful when using vSphere Replication for encrypted virtual machines together with NKP, see the documentation about "Replicating Encrypted Virtual Machines".
Note: vSphere Replication 8.4 does, as of today, not yet supported vSphere 7.0 U2.
Q: Where is Native Key Provider-data being stored on vCenter?
- The data, as well as the main private key for NKP, is stored encrypted in the vCenter database ("VCDB") on the vCenter Server Appliance.
- Additionally it is stored in the Config Store on individual ESXi hosts in an encrypted form.
As the NKP is saved in the vCenter database, it is also included in the File-based vCenter backups you can configure in the VAMI/venter Server Management Interface (which is strongly recommended, also in addition to a snapshot-based backup). Ensure your vCenter backups are encrypted and saved to a secure backup location.



Does NKP can store and import security keys from HSM? or it’s necessary to use any other KMS
No, HSM cannot be used. It was never meant as a full replacement compared to other Enterprise KMS solutions. You would need to use any other supported KMS.
if i decide to use the native key provider on hosts without tpm (untick the optipn in pic4) is it possible to change that later?
or do i have to recreate a new nkp then if it would be the case?